- Crypto Uncomplicated
- Posts
- Why bridges are unsafe in America — and even more so in crypto
Why bridges are unsafe in America — and even more so in crypto
To quote Bernie Sanders, "Crumbling infrastructure!"

Crypto Uncomplicated is a free crypto newsletter distilling all the happenings in the crypto space. Unlock the full experience as a premium subscriber by signing up here. Last week, premium subscribers got a closer look at the hottest NFT-focused chains that pumped about 50% this week.
One of my favorite facts about America's crumbling infrastructure is that about 42% of the U.S.'s bridges are more than a half-century old and nearly 10% are considered structurally deficient.
Doesn't seem safe.
And yet, as shaky as our bridges sound, crypto's bridges are somehow even shakier. As this week's nearly $200 million hack of the Nomad bridge reminded us, they remain some of the juciest targets in crypto. But what is a "bridge," and what made this hack — the eight largest in history by dollar amount — even more unique in the way it was carried out? Let's dig in.
Crypto Bridges
In crypto, ecosystems generally need some help speaking to each other since they are usually two entirely on entirely different blockchains. The Ethereum blockchain, for example, has no way of talking to the Bitcoin blockchain as it's enabled by entirely different code. In order to "bridge" the gap between them, developers can create smart contracts that essentially let users to put in "X" crypto coin and get "Y" token out. So, that equation could look like put in bitcoin, and get out "wrapped bitcoin" on the ethereum network. It's just an ethereum-native way to issue an IOU that can later be redeemed for bitcoin on the other side of the bridge. Neat!
Since bridges usually require a centralized storage of funds, they tend to be an obvious place for attackers to spend their time exploiting insecurities. In fact, about $2 billion worth of tokens have been stolen from bridges in 2022, according to Chainalysis estimates. That figure includes the Ronin Bridge attack earlier this year, which saw the protocol lose $625 million in ether and USDC after being targeted by the North Korean hacking group Lazarus. Not neat!
Frequently, attackers basically unlock ways to fake transactions that the bridge's code is tricked into believing are genuine. So, for example, you could fake a deposit of bitcoin into the bridge, and withdraw real ethereum on the other side. If you submit this fake transaction and it gets approved, you can often repeat it again and again long before a bridge's team even realizes they are getting robbed. (Interestingly, if a team does catch it in time it doesn't usually mean death. Thorchain, for example, has continued to grow after earlier exploits were patched.)
On Monday, attackers targeted Nomad — a bridge that enabled swaps between Avalanche (AVAX), Ethereum (ETH), Evmos (EVMOS), and other blockchains.
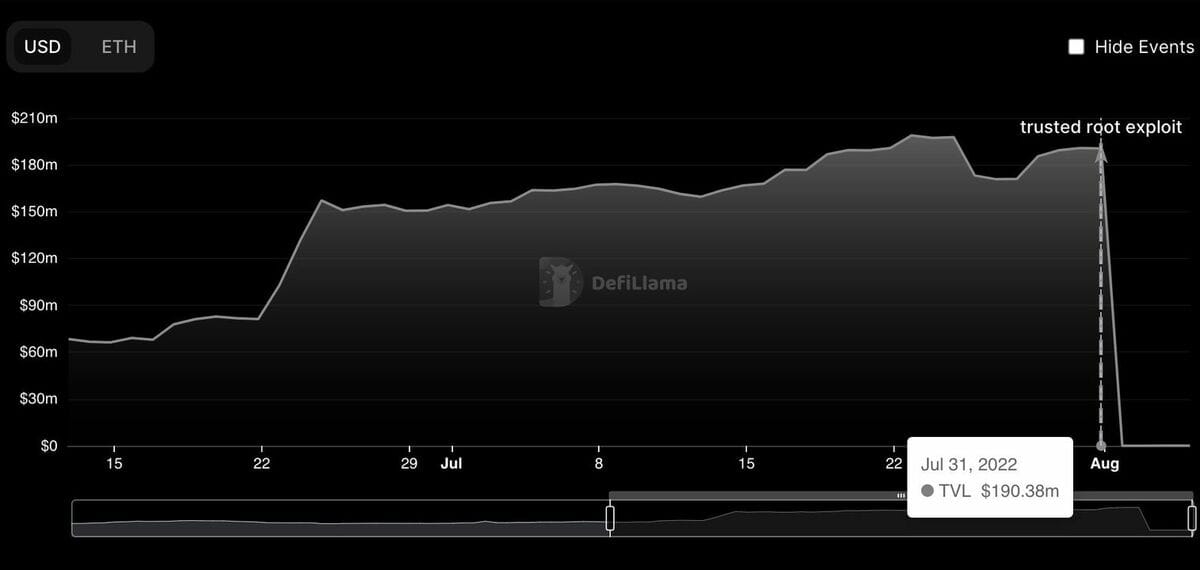
The Nomad funds locked tanked from $190 million to $0 in about a day. (Source: Analytics platform DeFi Llama)
What makes Nomad's hack unique, however, is that the first attack to successfully strike, basically published the blueprint publicly. The first attacker had figured out a way to effectively cash a blank check. Anyone watching would have been able to copy the transaction's code, swap the wallet address to direct to their own, and they, too, could essentially print their own bag of money. Of course, that presents some major ethical dilemmas.
On the one hand, some good samaritans could see this playing out and decide to "steal" the funds on the premise that they are the real good guys and they are only taking it to protect it from the bad guys who could now come and steal it pretty easily. And, indeed, that's exactly what some so-called "white hat hackers" did. About $10 million flowed back into the bridge once the dust settled. But what about the other $180 million?
Well, it remains to be seen. Nomad says it would let anyone who took funds from the bridge keep 10% of what they took — no questions asked. So if you stole $1 million you'd be able to keep $100,000 as a reward (and sleep at night.) Not bad. Or, you can hope no one ever finds out and keep everything.
In the end, crypto security firm Peckshield calculated that more than 41 addresses drained the bulk of the stolen funds ($152 million, or 80% of it all.)
It could be that the number of funds return climbs over the coming days, but I wouldn't be holding my breath. Unlike stealing in the real world, a lot of exploits aren't really looked at as "stealing" by a lot of people participating. It's simply interacting with a contract. If it has flaws, that's not the "thief's" fault. Then again, I wouldn't be so sure if the shoe were on the other foot in the way the contract operated. (Anyone who has ever tried to buy a bag of chips from a vending machine only to watch in horror as it gets stuck knows this feeling too well.)
Decentralized finance has come a long way, but until some of these hacks become less and less common, it's really hard to feel safe crossing any bridge. Crypto, or otherwise.
Crypto Uncomplicated is a free crypto newsletter distilling all the happenings in the crypto space. Get exclusive, expert insights on how to play the increased volatility as a premium subscriber by signing up here.